66% of IT professionals say unauthorized users can access their networks; 16% believe unauthorized users have access to their entire networks
Despite the increasing number of data breaches and more than 3.9 billion data records worldwide being lost or stolen since 2013, organizations continue to believe perimeter security technologies are effective against data breaches. This is one of the many findings of the third-annual Data Security Confidence Index released today by Gemalto.
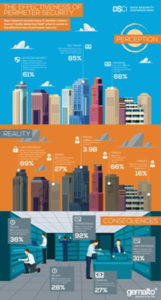 According to the press release, of the 1,100 IT decision makers surveyed worldwide, 61% said their perimeter security systems (firewall, IDPS, AV, content filtering, anomaly detection, etc.) were very effective at keeping unauthorized users out of their network. However, 69% said they are not confident their organization’s data would be secure if their perimeter security was breached. This is up from 66% in 2015 and 59% in 2014. Furthermore, 66% believe unauthorized users can access their network and nearly two in five (16%) said unauthorized users could access their entire network.
According to the press release, of the 1,100 IT decision makers surveyed worldwide, 61% said their perimeter security systems (firewall, IDPS, AV, content filtering, anomaly detection, etc.) were very effective at keeping unauthorized users out of their network. However, 69% said they are not confident their organization’s data would be secure if their perimeter security was breached. This is up from 66% in 2015 and 59% in 2014. Furthermore, 66% believe unauthorized users can access their network and nearly two in five (16%) said unauthorized users could access their entire network.
According to the research findings, 78% of IT decision makers said they had adjusted their strategies as a result of high profile data breaches, up from 71% in 2015 and up 53% in 2014. 86% said they had increased spending on perimeter security and 85% believe that their current investments are going to the right security technologies.
Despite the increased focus on perimeter security, the findings show the reality many organizations face when it comes to preventing data breaches. 64% of those surveyed said their organizations experienced a breach at some time over the past five years. More than a quarter (27%) said they experienced a breach in the past 12 months, with a similar number of IT decision makers (30%) reporting the same frequency in 2015. This suggests that organizations have not made significant improvements in reducing the number of data breaches despite increased investments in perimeter security.
Jason Hart, VP and CTO for Data Protection at Gemalto said, “This research shows that there is indeed a big divide between perception and reality when it comes to the effectiveness of perimeter security. The days of breach prevention are over, yet many IT organizations continue to rely on perimeter security as the foundation of their security strategies. The new reality is that IT professionals need to shift their mind set from breach prevention to breach acceptance and focus more on securing the breach by protecting the data itself and the users accessing the data. While companies are confident in the amount of spending and where they are spending it, it’s clear the security protocols they are employing are not living up to expectations. While protecting the perimeter is important, organizations need to come to the realization that they need a layered approach to security in the event the perimeter is breached. By employing tools such as end-to-end encryption and two-factor authentication across the network and the cloud, they can protect the whole organization and, most importantly, the data.




