By Sandeep Karan, Head – Information & Cybersecurity
Introduction
We use a variety of applications to perform daily tasks in our day-to-day lives, both professional and personal. With more technological dependence, each application necessitates security and use of password, which in turn necessitates the need for as many passwords as applications used. To make our lives easier, we tend to use easy-to-remember passwords, such as date of birth or anniversary, first name + last name combination, nick names or a mix with one of the dates or appending running serial number. Many a times, we may use the same passwords across multiple applications for personal and professional life.
While making our lives simple with easy-to-remember passwords, we unknowingly make the work of a hacker easy as well by using such easy-to-guess passwords. In today’s IT world, relying only on username and password is not enough to protect critical data and systems against the growing number of sophisticated cyber-attacks.
According to Verizon 2022 Data Breach Incident Report, 82% of breaches involved a ‘Human Element’. In 2015, cyber breach via stolen credentials was around 26%, which grew to 45% by 2017 and soared to over 80% by 2021. On the contrary, breach by exploiting vulnerability was around 55% in 2015 which reduced to 45% by 2017 and by 2021 it had further reduced to around 25%. The number says it all – cyber breach using stolen credential or password is a hacker’s favorite.
The Past: Cyberattacks using stolen credentials in 2021
February 2021 will be remembered for the supply chain cyberattack involving software from SolarWinds, where several U.S. government agencies were compromised. The hackers deftly exploited a key vulnerability in the cybersecurity services provider’s network monitoring software, which then allowed them to enter laterally and gain unauthorized access.
While this has not been confirmed, reports indicate that the root cause of the cyber-incident was in fact a weak password, and that it was publicly accessible through a misconfigured GitHub repository.
Similarly in November 2021, GoDaddy reported a major security breach. The incident compromised GoDaddy accounts of over a million WordPress customers. Attacker(s) had gained unauthorized entry into GoDaddy’s Managed WordPress hosting environment, leveraging a compromised passcode to facilitate the hacking of the company’s provisioning system.
The GoDaddy incident exposed the customer numbers and email addresses of about 1.2 million customers, besides compromising the original WordPress Admin passwords and several SSL private keys.
Another example from is Verkada, where hackers breached the company’s systems using an admin password leaked online in a misconfigured customer support server.
An important point to note here is that, now-a-days, there are a number of online applications that can verify whether an email ID or phone number has been breached by hackers.”
The Present: Adoptive Authentication
For strong passwords, it is always best to use different passwords for different applications and not writing them down, but just remembering them. According to SIMFORM’s survey, an average person has at least 40 apps installed on their mobile phone. Remembering 40 complex and different passwords can be challenging.
To address this, Password Manager applications are becoming more and more popular. A password manager is an app that generates new, random passwords for the sites you visit and stores them in a secure, virtual vault. The next time you visit a site that requires you to log in, the password manager will automatically fill in your credentials. The features of such apps are not limited to username and password – password managers can save sensitive data such as name, address, and credit card information while others can save important documents, medical information, and safe codes.
But the question remains, is depending only on username and complex password enough?
With Multi-Factor Authentication (MFA), the system users must provide at least two (or more) “factors” when they wish to access applications, network, and resources. Most common methods to achieve this are
- Something you may know – including a PIN, or answer to a security question
- Something you may have – including a smartphone, smart card, or a one-time pass token,
- Something unique to you – including biometrics such as retina scans, fingerprint or voice recognition
This gives additional protection, over and above the username and password combination. But MFA may not be a full-proof plan as there are ways to bypass MFA as well and it can become challenging due to its double authentication process. Hence, when providing access, additional risk analysis needs to be performed and based on the outcome, appropriate access to be provided to resources. This approach is known as Adaptive Authentication.
Often referred to as a risk-based authentication framework, Adaptive Authentication is designed to select the appropriate authentication factors with an eye on the perceived risk and associated user behavior. Factors such as the user’s geographical location, the device used, and the role of the user can play an important part in whether (if at all) and what access should be granted. Think of an advanced MFA model!
Adaptive Authentication offerings deliver a higher degree of security as compared to two-factor authentication – the most commonly used user authentication scheme. The latter is quite predictable, and you know that you will need to enter a passcode.
However, hackers know that too.
How do you confirm that the passcode made it to the right person? You can’t, and that is what makes the whole idea of Adaptive Authentication so much more relevant to the end-user.
Adaptive Authentication protocols are designed to continuously monitor the user’s given security posture, incorporating extended authentication factors as necessary. It is remains aware of the typical activities for the user, so that when a suspicious event occurs, the safety protocols isolate the affected user and protect key business applications.
Some Adaptive Authentication solutions even leverage Machine Learning (ML) and Artificial Intelligence (AI) to detect new attack vectors before they become known, helping IT personnel in fighting back cyberattacks.
Unlike standard authentication protocols, Adaptive Authentication is designed to adapt to the evolving situation. The paradigm is built as the epitome of identity and access management amidst the challenge of modern cyber threats.
The Future: Improving IT security with Passwordless Authentication
There is a saying, “hackers do not break-in, they log in”. The next level in IT security is going “passwordless”. If there are no passwords, hackers will not have anything to steal.
Passwordless Authentication was designed to allow user access to applications or IT systems without having to supply a passcode or trying to remember the answer to a security question. The user, instead, can provide some alternate evidence, including a proximity badge, their fingerprint or retina scan, or a hardware token. The paradigm is often leveraged in combination with Single Sign-On and Multi-Factor Authentication solutions to help deliver an improved user experience, while strengthening security and reducing cost and complexity in IT operations.
Passwordless Authentication helps strengthen IT security by removing the need for risky passcode administration practices and minimizing potential attack vectors. It is also focused on delivering an improved user experience paradigm by eliminating the oft-quoted secrets and passwords fatigue.
Leveraging Passwordless Authentication, we no longer have to rely on passwords that need to be memorized or security question answers which must be recalled. Users can be migrated to:
- USB devices (FIDO2-compliant keys), physical tokens, or Proximity badges
- Software certificates or tokens
- Fingerprint, retina scanning, or voice/facial recognition,
- Mobile phone-based applications
In a corporate environment, for devices and applications to be passwordless while maintaining seamless working conditions, additional layer of Single-Sign On (SSO) plays a crucial role.
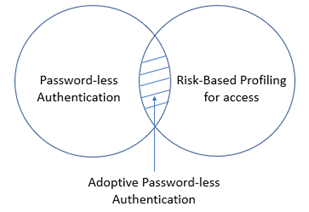
- Adoptive Passwordless Authentication
Using passwordless method, in addition to risk-based profiling for authentication creates Adoptive Passwordless Authentication system.
Figure 1: Adoptive Password-less Authentication
Adoptive Passwordless Authentication is a journey and organizations are likely to take time to adopt has it requires considerable amount of effort, cost and time to implement when compared with other methods of authentication.
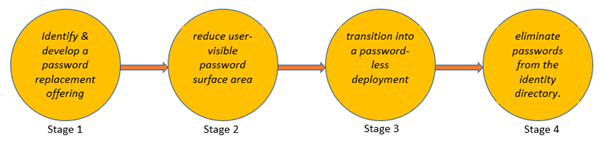
According to Microsoft’s Passwordless Strategy, one needs to:
- Identify, develop, and implement a password replacement tool or offering
- Reduce the user-visible password surface area
- Transition toward a password-less deployment, and then
- Eliminate the need for passwords from the existing identity directory
Figure 2: Strategy of Adoptive Passwordless Authentication
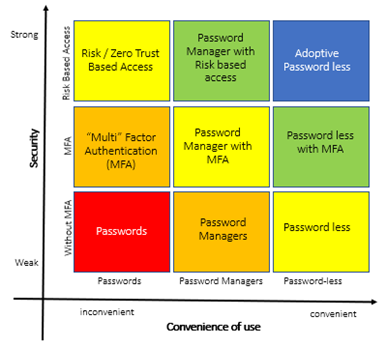
The below heat matrix represents the best journey that can be opted for Adoptive Passwordless Authentication:
Figure 3: Authentication Heat Matrix
Although, the importance and need for passwordless and risk-based authentication or even Adoptive Passwordless Authentication is rising, there are still no pre-defined paths and timeframes for the journey. Any organization needs to choose their own path in the journey to achieve complete IT security, depending upon current maturity level, risk appetite, effort and investment and change management requirements.
References: –
2022 Data Breach Investigation Report (DBIR) | Verizon
The Most Significant Password Breaches Of 2021 | Expert Insights
App Usage Statistics 2021 that’ll Surprise You (Updated) (simform.com)