Delivers the first solution to automate both discovery and remediation actions for potential CloudBleed exposures; Symantec Customers Can Quickly and Easily Respond to CloudBleed Vulnerability
Within days of receiving news of the CloudBleed vulnerability that potentially compromised millions of user accounts in cloud applications, Symantec has released an automated solution to identify and resolve potential exposures to current Symantec ProxySG customers. Symantec is uniquely positioned to deliver this comprehensive and automated solution to customers by leveraging integrations between its CloudSOC Cloud Access Security Broker (CASB) and the broader Symantec security portfolio.
Following the incident, Symantec analysts mapped the vulnerable CloudBleed web URLs to specific cloud applications and CloudSOC Audit identified more than 2,000 applications that were potentially affected by CloudBleed. As a result, CloudSOC Audit, the CASB component for discovering Shadow IT, now tracks the CloudBleed vulnerability as an at risk attribute for cloud applications. Symantec customers using CloudSOC Audit can now automatically identify users of cloud applications both on-network and off-network who could be at risk of compromise due to CloudBleed.
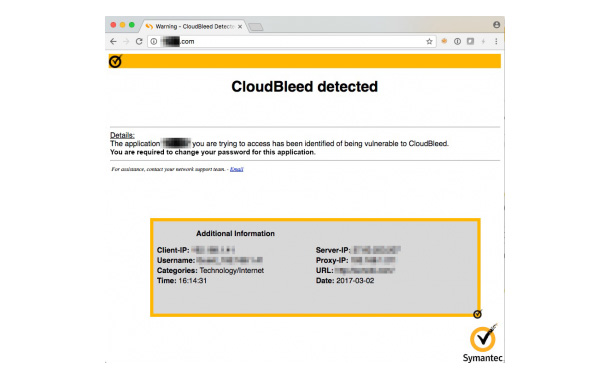
By leveraging the CloudSOC Audit AppFeed (provided via the Symantec Global Intelligence Network), Symantec ProxySG customers will be able to set a policy to automatically send alerts to users of at risk cloud applications. This notification, triggered by the use of a vulnerable application, can instruct users to update their password and inform them that their cloud account has potentially been exposed.
Symantec CloudSOC provides organizations with a unique level of visibility and automated control over their use of cloud applications and services through the integration of ProxySG, Web Security Services, Endpoint Protection, DLP and the Symantec Global Intelligence Network. Through this integration, customers benefit from the following capabilities:
CloudSOC Audit tracks intelligence on over 20,000 cloud applications based on 90+ different risk attributes, now including the CloudBleed vulnerability
CloudSOC gets more log data from more sources to provide broader visibility over Shadow IT. Audit compiles log data from Symantec ProxySG and Web Security Service cloud proxy as well as third-party gateways, firewalls and SIEM systems to discover the use of cloud applications within an organization. Unlike other CASB solutions, CloudSOC Audit can also collect log data from Symantec Endpoint enabling Shadow IT visibility over off-network use of cloud applications.
ProxySG automatically enforces policy controls over the use of cloud applications based on integrated intelligence from CloudSOC Audit delivered through an AppFeed subscription from the Symantec Global Intelligence Network. Policy controls in ProxySG include block, alert, and continue pages that can contain custom messages to educate the user. These custom notifications could be used to recommend alternative cloud applications, deliver security instructions such as a request to update account settings, or general security education for end users.