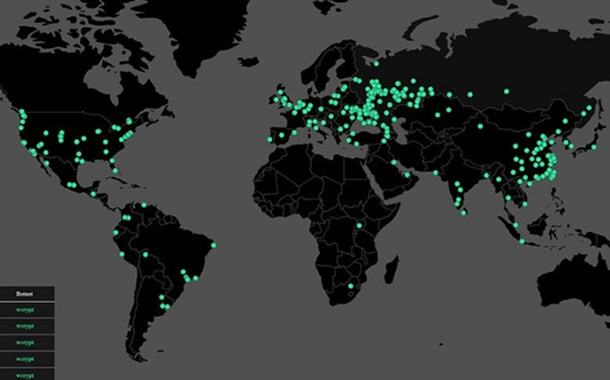
With over 300,000 computers in 150 countries already infected and the numbers continuing to grow, WannaCry is turning out to be the biggest attack of its kind. Microsoft has released patch for its complete portfolio of operating systems but the threat is here to stay!
The menace of cybersecurity reached new levels when a new ransomware attack, unprecedented in magnitude, plagued computers across the world. The quickly spreading global virus, WannaCry was launched on Friday 12th May 2017. Being addressed by different names such as WannaCrypt WanaCrypt0r 2.0, Wanna Decryptor across the internet, the ransomware spread across servers and organizations in no time, becoming a nuisance in as many as 70 countries over the weekend.
Although there has been wide-spread knowledge of the attack over the last two days, the ransomware is still active and has been spreading rapidly. Specific to Windows PCs, it has been encrypting information in affected PCs and asking a sum of 300 USD in Bit coins as ransom for the release of the information. Ram Punamaraju, CEO & CoFounder, Yitsol said, “The ransomware threat is a challenging one for the networks across the globe, spread through emails, the human element responsible for its spread is equally responsible for the threat to grow.”
[quote font=”tahoma” font_size=”13″ font_style=”italic” color=”#262626″ bgcolor=”#f2f2f2″] “The creators of WannaCry have integrated this critical exploit into its worm module (initial dropper), thus taking advantage of the vulnerable instance of SMB protocol to propagate.” –
“The creators of WannaCry have integrated this critical exploit into its worm module (initial dropper), thus taking advantage of the vulnerable instance of SMB protocol to propagate.” –
Sunil Gupta,
President and COO,
Paladion Networks
[/quote]
Microsoft has released patch for its complete portfolio of operating systems but with the enormity of the widespread window PC networks and the fact that most of them aren’t prompt in installing updates and patches, the ransomware has continued with its attacks across the globe.
How it started and who is behind it?
In quite recent news, a league of black-hat hackers known as Shadow brokers broke into the servers of the National Security Agency, United States’ apex cybersecurity body. They leaked the US Spy agency’s hacking tools and vulnerabilities on public domain. One of these vulnerabilities, called Eternal Blue exploit, which relied on a SMB Exploit to hack into other connected / networked PCs in a network.
[quote font=”tahoma” font_size=”13″ font_style=”italic” color=”#262626″ bgcolor=”#f2f2f2″] “Enterprises constantly struggle to stay on top of regular patching cycles as this can impact day-to-day operations in some cases.” –
“Enterprises constantly struggle to stay on top of regular patching cycles as this can impact day-to-day operations in some cases.” –
Kartik Shahani,
Integrated Security Leader
IBM ISA
[/quote]
Like previous ransomware attacks, WannaCry spreads by phishing emails but also uses the EternalBlue exploit and DoublePulsar backdoor developed by the U.S. National Security Agency (NSA) to spread through a network which has not installed recent security updates to directly infect any exposed systems. According to John Miller, Sophos Threat Researcher, “Despite encouraging reports of waning threat activity, WannaCry continues to pose significant risks. Given this malware’s effective repropagation mechanisms, virtually any organization that hasn’t applied Microsoft’s recommended mitigation mechanisms is at potential risk of attempted WannaCry propagation.”
[quote font=”tahoma” font_size=”13″ font_style=”italic” color=”#262626″ bgcolor=”#f2f2f2″] “Kerala and Andhra Pradesh have been affected partly. We are keeping a close eye on the situation and strengthening our cyber system.” –
“Kerala and Andhra Pradesh have been affected partly. We are keeping a close eye on the situation and strengthening our cyber system.” –
Ravi Shankar Prasad
IT minister
[/quote]
Trying to check the spread of the attack, a ‘critical’ patch was issued by Microsoft on 14 March 2017 to remove the underlying vulnerability for supported systems. Also, those still running exposed older, unsupported operating systems were initially at particular risk, such as Windows XP and Windows Server 2003, but Microsoft has now taken the unusual step of releasing updates for these.
What is the impact?
WannaCry has infected more than 300,000 computers in over 150 countries already. The software is capable of demanding ransom payments in the crypto currency Bitcoin in 28 languages which answers its viability as a global attack. Top security agencies like Europol have described it as ‘unprecedented in scale’. In its initial stages, the virus affected Telefónica and several other large companies in Spain, as well as parts of Britain’s National Health Service (NHS), FedEx, Deutsche Bahn, and LATAM Airlines. Around the same time, similar targets in at least 99 countries were also reported to have been compromised.
[quote font=”tahoma” font_size=”13″ font_style=”italic” color=”#262626″ bgcolor=”#f2f2f2″] “India is getting hit hard by such attacks as India has a large number of Windows users who do not have proper security patches applied and rely on inadequate internet security.” –
“India is getting hit hard by such attacks as India has a large number of Windows users who do not have proper security patches applied and rely on inadequate internet security.” –
Sanjay Katkar
MD & CTO
Quick Heal Technologies
[/quote]
Specific only to Windows PCs, WannaCry appears to travel across corporate networks, spreading quickly through file-sharing systems. Kartik Shahani, Integrated Security Leader, IBM ISA said, “The incident could have been avoided if critical patches were applied in time throughout companies across all industries. Enterprises constantly struggle to stay on top of regular patching cycles as this can impact day-to-day operations in some cases. Companies will need to have an incident response plan in place to quickly recover and also ensure that employees, suppliers and others who work with them receive regular security training.” Sunil Gupta, COO, Paladion Networks added, “The creators of WannaCry have integrated this critical exploit into its worm module (initial dropper), thus taking advantage of the vulnerable instance of SMB protocol to propagate.” The corporate computers are typically controlled by IT departments that choose when to send updates to computers. So if one computer is vulnerable, it’s likely all the computers on a corporate network are too, making it easy for WannaCry to have a large impact. It has further been analyzed that networks of computers, like schools, companies, hospitals and businesses, are particularly vulnerable. That’s because security researchers say the ransomware is spread through standard file sharing technology used by PCs called Microsoft Windows Server Message Block or “SMB” for short. It also appears able to spread to other computers outside corporate networks. Researchers have already found variants of the attack, so there isn’t just one way it works
[quote font=”tahoma” font_size=”13″ font_style=”italic” color=”#262626″ bgcolor=”#f2f2f2″]
“It is imperative that businesses everywhere update their operating systems, their security software and educate their users against phishing attacks. This is a best practice to reduce the risk from any attack.”
Sunil Sharma
Vice President
Sales at Sophos, India & SAARC
[/quote]
Although CERT-In has come out saying that it has not received any formal report of cyber attack on India’s vital networks by Wanna Cry, reports are doing rounds that India might be among the worst affected countries from the ransomware attack. There have been unconfirmed reports that the Indian government has shut down some ATMs all over the country as a preventive measure against the cyber attack. According to the reports Automated Teller Machines (ATMs) are highly vulnerable to such malware attacks, with most of them presently running on old versions of Microsoft’s Windows OS. This makes a software security patch update a necessary exercise for the total of 2.2 lakh ATMs in India, of which many old ones run on Windows XP. Sanjay Katkar, MD & CTO, Quick Heal Technologies said, “Cybercriminals are not discriminating while attacking and spreading malware. India is getting hit hard by such attacks as India has a large number of Windows users who do not have proper security patches applied and rely on inadequate internet security.”
[quote font=”tahoma” font_size=”13″ font_style=”italic” color=”#262626″ bgcolor=”#f2f2f2″]
“Organizations isolate infected devices immediately by removing them from the network as soon as possible to prevent ransomware from spreading to the network or shared drives.”
Rajesh Maurya
Regional Vice President
India & SAARC
Fortinet
[/quote]
IT minister Ravi Shankar Prasad said, “Kerala and Andhra Pradesh have been affected partly. We are keeping a close eye on the situation and strengthening our cyber system. In two village panchayats of Kerala, computers were hit with messages demanding USD 300 in virtual currency to unlock the hacked files.” As MHA officials closely monitor the situation, the Reserve Bank of India (RBI) has issued an advisory asking all banks to ‘put in place a software update at ATMs to prevent their systems from a malware that has attacked payment systems across the world.’
[quote font=”tahoma” font_size=”13″ font_style=”italic” color=”#262626″ bgcolor=”#f2f2f2″] “WannaCry marks a new era in distributed cybercrime. Organizations need to fundamentally change their approach to managing and prioritizing vulnerabilities in their networks.”
“WannaCry marks a new era in distributed cybercrime. Organizations need to fundamentally change their approach to managing and prioritizing vulnerabilities in their networks.”
Ravid Circus
VP Products,
Skybox Security
[/quote]
Quickheal received over 700 distressed calls regarding the spread of this ransomware. Among the attempted attacks by the malicious WannaCry ransomware, 60% were targeted towards enterprises and 40% towards individual customers. The top five states with maximum detections are West Bengal, Maharashtra, Gujarat, NCR (Delhi), and Odisha.
Tips to secure your PC
From the enterprise perspective, when vulnerabilities exist and patches are made available, it is the responsibility of the Security Administrators to patch up the systems under their control. Microsoft had released a patch MS17-010 way back in March to address this security threat. It has been proved beyond doubt that Security Administrators and the entire process of reviewing the laid down procedures for ensuring patch management has taken a severe beating. MS17-010 has been provided as an update globally. As a special one-off case, Microsoft has also released the update for XP and 2003 operating systems.
[quote font=”tahoma” font_size=”13″ font_style=”italic” color=”#262626″ bgcolor=”#f2f2f2″]
“Businesses should ensure a backup is available that is not shared on the network and block encrypted password protected attachments from email gateways.”
Bhaskar Bhaktavatsalu
Managing Director
India and SAARC
Check Point Software Technologies
[/quote]
Security players have been trying to educate their customers. Indian Computer Emergency Response Team (CERT-In) has also come out with a list of do’s and don’ts and webcast on how to protect networks from the global ransomware attack.
Following are some tips with which you can safequard your PC from WannaCry:
- Download and implement MS17-010 patch, which can be found over here: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
- Block executable files from being transmitted via eMails.
- Isolate the affected system from your Network.
- Restore the encrypted files from the backup or from system restore point (if enabled).Don’t enable macros in documents received as attachments via email.
- Do not open attachments if received from unsolicited source.
- Deploy and maintain a backup solution.
- And last, but most important, protection of Mail server at Gateway Level with Mailscan to prevent delivering of such suspicious emails
The information provided above will help you to protect your system from being victim of Ransomware.
Finally,
The WannaCry ransomware attack has once again confirmed the balance of power in the cybersecurity domain. It has reiterated the fact that cyber security is neither a one off practice nor is it a guarantee from any and every attack. It is a well known fact that cyber attackers are always one step ahead of the security companies and this is a well established fact. The key to security is a gradual unending process, which is collaboration between the enterprises and security vendors. As Budiman Tsjin, Senior Technical Consultant, Asia, RSA said, “It is important to detect and find out which machines have been infected and how bad is the spread of the infection. If you have not, better start documenting detection controls and response procedures for ransomware. This threat is here to stay and will continue to evolve and impact our lives significantly.”
By: Chitresh Sehgal – csehgal@accentinfomedia.com