Introduction
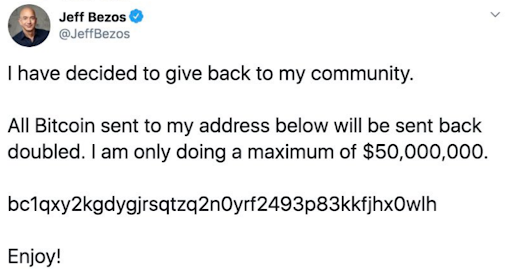
A large number of high-profile Twitter accounts have been taken over on Wednesday in what seems to be a social engineering attack against some of Twitter’s employees. This included the accounts of Barack Obama, Joe Biden, Elon Musk, as well as the official accounts of Uber, Apple, and cryptocurrency exchanges.
The compromised accounts were then used to promote a cryptocurrency scam that promised to double the amount of bitcoins sent to a certain wallet address only for a limited time.
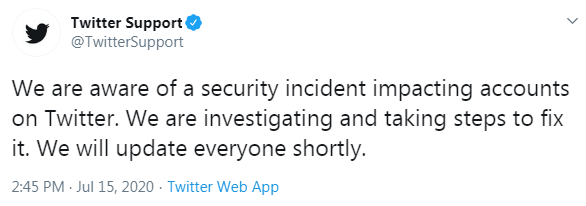
Additionally, compromised accounts of large cryptocurrency exchanges and leaders in the cryptocurrency community even claimed to be partnering with a made up organization called “CryptoForHealth”:
The website mentioned in those tweets, cryptoforhealth[.]com, was registered on the same day of the attack and claimed to be helping the community after the financial losses caused by COVID-19. In reality, the website was asking for bitcoin to be sent to the same wallet address that appeared in the tweets.

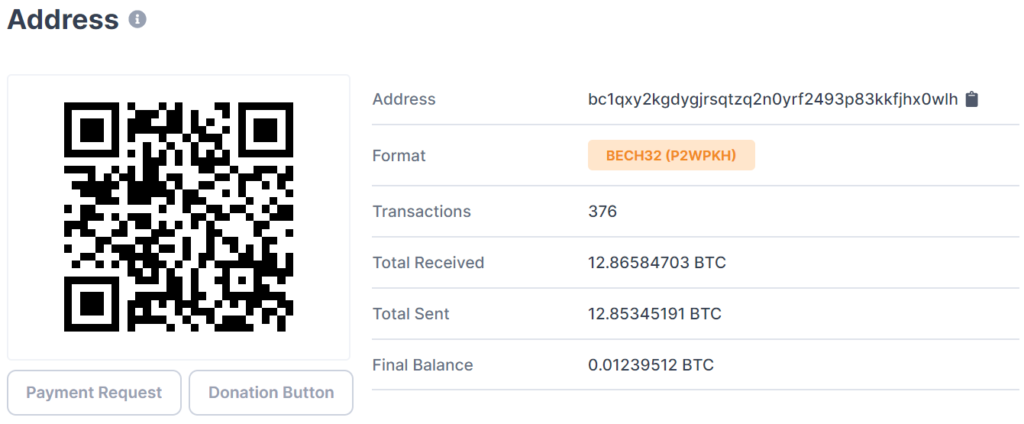
Although the attack was short-lived and Twitter quickly locked down and recovered any affected accounts, a look at the bitcoin wallet address shows that the attackers still managed to get away with 12.85BTC, nearly $120,000, and were already transferring the money to further Bitcoin accounts to cash out:
Attack Vector
There are a few methods by which such an attack could have occurred.
Twitter announced social engineering techniques were used to gain access to their internal systems.
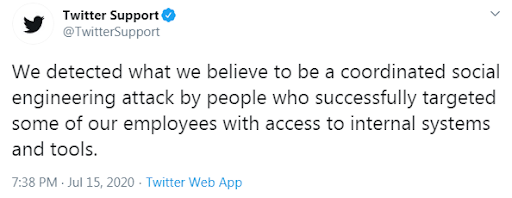
Such a compromise via social engineering attack could have started by using several possible infection vectors. One common possibility is spear-phishing email attack, either delivering an attached malware or a link to a phishing page. In both cases it is often accompanied with some kind of social engineering in order to motivate the user into executing the attached payload, or to enter his credentials into a fraudulent phishing page.
A possible attack vector that also corresponds with the previous explanations is voice phishing or Vishing. This is a social engineering tactic of phishing calls to employees in order to gain trust, harvest details and deceive them to take actions. Over the last few months, more and more organizations have reported that their employees were targets of such Vishing calls.
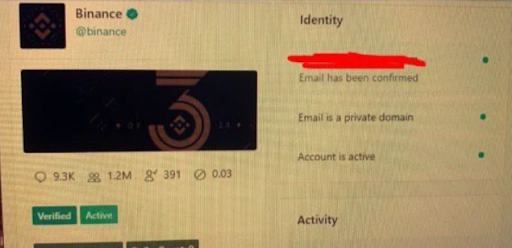
Motherboard offers another potential scenario, in which the attackers had internal cooperation with Twitter employees they paid to change the e-mail addresses behind the targeted accounts using a Twitter internal tool.
Allegedly, screenshots of this tool have been shared in underground hacking forums:
A Long History of Breaches
This is not the first time the privacy of users in the social platform was impacted by its employees, nor the first time that Twitter employees were responsible for sensitive data disclosure.
The account of Twitter’s own CEO Jack Dorsey was compromised a few months ago after his phone number was taken over in a SIM swapping attack. Last year, two employees were accused of abusing their access to internal Twitter resources and helping Saudi Arabia spy on dissidents living abroad.
Although Twitter has not yet shared the full details of this incident, we can see that different root causes in previous cases have led to similar results. Whether it is disgruntled employees or tailored social engineering attacks, the true problem is the difficulty in limiting access to internal assets and preventing them from becoming a single point of failure.
This time, however, it seems that Twitter is taking action to prevent such incidents from occurring again in the future, by making tools such as the one presumably used in this attack less accessible:
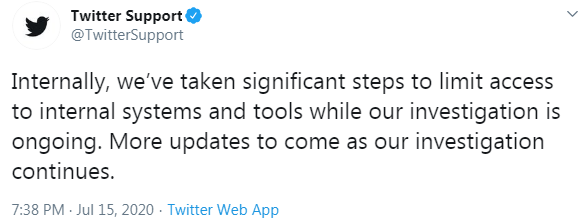
If anything, Twitter’s compromise shows that in today’s world of increasing data loss events, organizations have little choice but to take action to protect sensitive data. Confidential employee and customer data, legal documents, and intellectual property are being exposed to unwanted parties on a daily basis.
Quote: Lotem Finkelstein, Head of Threat Intelligence, Check Point Software Technologies
“This is not the first time the privacy of users in the social platform was impacted by its employees, nor the first time that Twitter employees were responsible for sensitive data disclosure.
The account of Twitter’s own CEO Jack Dorsey was compromiseda few months ago after his phone number was taken over in a SIM swapping attack. Last year, two employees were accused of abusing their access to internal Twitter resources and helping Saudi Arabia spy on dissidents living abroad.
Although Twitter has not yet shared the full details of this incident, we can see that different root causes in previous cases have led to similar results. Whether it is disgruntled employees or tailored social engineering attacks, the true problem is the difficulty in limiting access to internal assets and preventing them from becoming a single point of failure.
This time, however, it seems that Twitter is taking action to prevent such incidents from occurring again in the future, by making tools such as the one presumably used in this attack less accessible:
If anything, Twitter’s compromise shows that in today’s world of increasing data loss events, organizations have little choice but to take action to protect sensitive data. Confidential employee and customer data, legal documents, and intellectual property are being exposed to unwanted parties on a daily basis.”
Conclusion
Social engineering is not only effective to gain access to corporate assets; motivating twitter users to transfer $120K to an unknown wallet with fishy promises made by celebrities is an excellent example of malicious use of social engineering.
When we imagine potential cyber-security threats, we often imagine foreign adversaries hacking their way to steal intellectual property or engage in malicious activity. That is true in many cases but in reality, at least 30% of breaches involve internal actors from within the corporation.
Protection measures should address incidents from both internal and external threats.
Check Point CloudGuard SaaS blocks sophisticated phishing attacks that leverage social engineering techniques before they reach users, thus protecting organizations from their weakest link – end users. In addition, it prevents lateral movement of attacks within the organization by scanning and blocking internal threats in real time, stops account takeover attacks attempting to hijack employees accounts – even if their credentials were stolen, and prevents sensitive data leakage according to company policies – across both cloud email and productivity suite applications.Check Point Data Loss Prevention (DLP) pre-emptively protects your business from unintentional loss of valuable and sensitive information. Furthermore, it monitors data movement and empower your employees to work with confidence, while staying compliant with regulations and industry standard.