In the recent past, numerous Ransomware has been targeting Europe and using various methods, jumped laterally across the networks and propagated to other countries, effectively breaching all geo-political boundaries.
A new Ransomware dubbed as Bad Rabbit has been rapidly targeting systems across Europe and following the footsteps of WannaCry and NotPetya. However, unlike WannaCry, Bad Rabbit does not use Eternal Blue for spreading laterally, but uses Mimikatz to extract the credentials from memory and tries to access systems within the same network via SMB and WebDAV.
Apart from encrypting the files, it adds the string “encrypted” at the end of the file rather than changing the extension. Changing the file extension is quite prevalent with most of the ransomware. The primary mode of delivery is via a Fake Flash Player installer and upon execution by the user; it would start encrypting the files and then modify the Master Boot Record, reboot the system and display the Ransomware Note.
eScan actively detects and mitigates this threat. Users should always ensure that they update their computer systems with the patches that are made available by Software Vendors. They should always exercise caution whenever any website presents to you an executable to be downloaded.
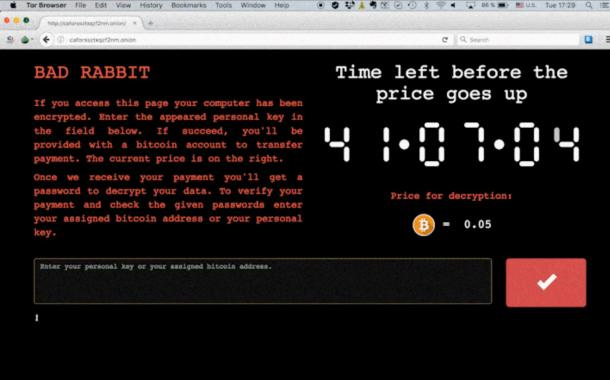
Ransom Note:
Oops! Your files have been encrypted.
If you see this text, your files are no longer accessible.
You might have been looking for a way to recover your files.
Don’t waste your time. No one will be able to recover them without our decryption service.
You can recover all your files safely. All you need to do is submit the payment and get the decryption password. Visit our web service at caforssztxqzf2nm.onion
Prevention Measures:
- Administrators should block all executable files from being transmitted via emails.
- Administrators should isolate the affected system in the Network.
- Administrator can restore the encrypted files from the backup or from system restore point (if enabled) for affected systems.
- Install and Configure eScan with all security modules active
- Users shouldn’t enable macros in documents.
- Organizations should deploy and maintain a backup solution.
Most important, organizations should implement MailScan at the Gateway Level for mail servers, to contain the spread of suspicious attachments