Persirai IoT Botnet Targeted 120,000 IP Cameras: TrendMircro Detects and Provides Threat Protection Solutions
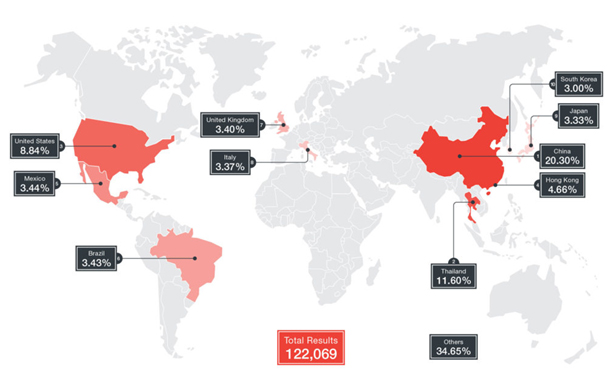
Trend Micro detected a new Internet of Things (IoT) botnet malware called Persirai. It was recently discovered targeting over 120,000 Internet Protocol (IP) cameras that are vulnerable to Persirai via Shodan. Many of these vulnerable users are unaware that their IP Cameras are exposed to the internet which makes it significantly easier for the perpetrators behind the malware to gain access to the IP Camera web interface via TCP Port 81. Trend Micro also provides solutions to protect against this threat.
IP Cameras typically use Universal Plug and Play (UPnP), which are network protocols that allow devices to open a port on the router and act like a server, making them highly visible targets for IoT malware. After logging into the vulnerable interface, the attacker can perform a command injection to force the IP Camera to connect to a download site via commands. After receiving commands from the server, the IP Camera will then start automatically attacking other IP Cameras by exploiting a zero-day vulnerability that was made public a few months ago. Attackers exploiting this vulnerability will be able to get the password file from the user, providing them the means to do command injections regardless of password strength.
Moreover, the affected IP Camera receives a command from the C&C server, instructing it to perform a DDoS attack on other computers via User Datagram Protocol (UDP) floods. Notably, Persirai can perform User Datagram Protocol (UDP) DDoS attack with SSDP packets without spoofing IP address.Trend Micro found that the C&C servers were using the .IR country code. This specific country code is managed by an Iranian research institute which restricts it to Iranians only and some special Persian characters which the malware author used.
The targeted IP Camera models are based on various Original Equipment Manufacturer (OEM) products. This development comes on the heels of Mirai—an open-source backdoor malware that caused some of the most notable incidents of 2016 via Distributed Denial-of-Service (DDoS) attacks that compromised IoT devices such as Digital Video Recorders (DVRs) and CCTV cameras—as well as the Hajime botnet.
In this event, a large number of these attacks are caused by the use of the default password in the device interface. Thus, users should change their default password as soon as possible and use a strong password for their devices. A strong password alone does not guarantee device security. IP Camera owners should also implement other steps to ensure that their devices are protected from external attacks. In addition to using a strong password, users should also disable UPnP on their routers to prevent devices within the network from opening ports to the external Internet without any warning.
“The burden of IoT security does not rest on the user alone—it’s also dependent on the vendors themselves, as they should be the ones responsible for making sure that their devices are secure and always updated. In line with this, users should make sure that their devices are always updated with the latest firmware to minimize the chance of vulnerability exploits. Users can look into solutions such as Trend Micro™ Security and Trend Micro Internet Security, which offer effective protection for threat’s to IoT devices using security features that can detect malware at the endpoint level,” said Nilesh Jain, Country Manager (India and SAARC), Trend Micro. “Connected devices are protected by security solutions such as Trend Micro Home Network Security, which can check internet traffic between the router and all connected devices. In addition, enterprises can monitor all ports and network protocols to detect advanced threats and protect from targeted attacks via Trend Micro™ Deep Discovery™ Inspector.”