Check Point Researchers have seen the same Iranian groups attacking with more large-scale attacks, at the levels previously seen.
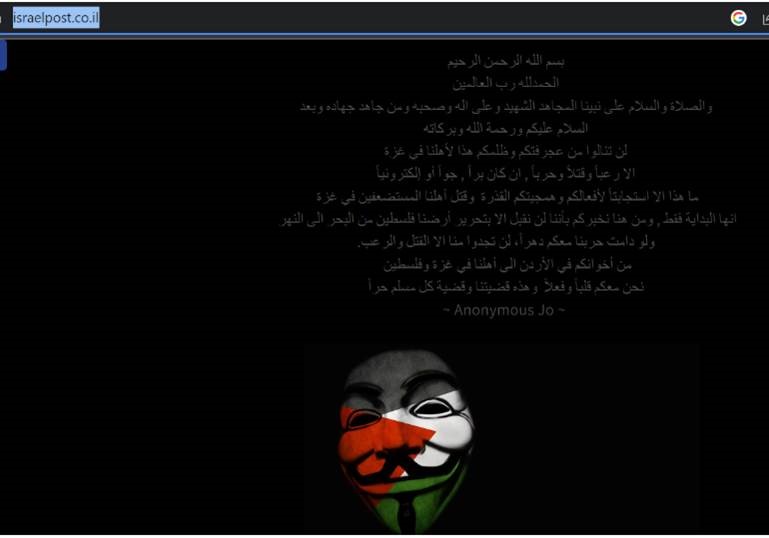
Defacements of websites and denials of service (DDoS) continue on almost a daily basis, even to the point of defacing the homepage of the Israeli Defense Forces and the Israeli Postal Services. Both had the following statement on their homepage for a few minutes, until it was taken down.
The group behind it referred to themselves as ‘Anonymous Jordan’ – an unknown group with no previous records (so this could be just a name they gave themselves for this attack). So all in all – pretty much the same.
This is how the webpage looked like and an English translation of what they wrote:
“Your arrogance and injustice towards our people in Gaza will only harm you through terror, killing and war, whether on land, in the air or electronically. This is nothing more than a response to your dirty actions and the barbarity and murder of our vulnerable people in Gaza. This is just the beginning, and from here on we tell you that we will only accept the liberation of our land, Palestine, from the river to the sea. Even if our war with you lasts an eternity, you will find nothing from us but slaughter and terror. Anonymous Jo”
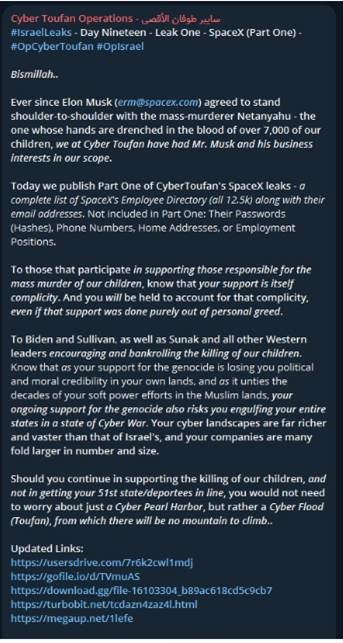
We also saw a rather interesting incident : Cyber Toufan, ) https://t.me/CyberToufan( the notorious group we’ve been corresponding about for a while and which does daily leaks to this day (around 35 large data leaks so far), said they attacked SpaceX due to Musk’s support of Israel.
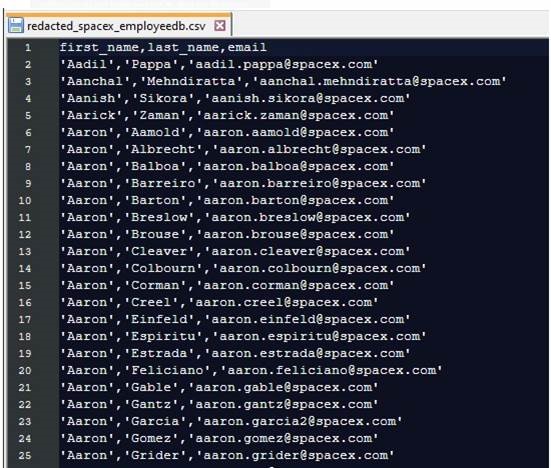
They shared a new leak, claiming to have hacked into SpaceX , and released a CSV file which contains 12,000 employee records with first & last names and their corresponding email addresses. The group claims that this is only partial data and that they also have their Passwords (Hashes), Phone Numbers, Home Addresses, or Employment Positions. Usually when such leaks happen, it can be a generated list from a source like LinkedIn or other open-sourced database, not a real hack, we cannot know for sure.
The extent of the information shared here is lower than previous leaks (which had thousands to hundreds of thousands of records including phones, full names, addresses, and at times even hashed passwords and the 4 digits of a credit card), but as said, they do claim that this is “part one”, referring to a potential part two with more information. Here is what they wrote and how this looked like. Due to this hack, Google blocked their page, but you can still see it from Apple.
This isn’t the first time this group referred to non-Israeli companies, as they shared a very big file with 1.8 million alleged records belonging to Berkshire eSupply on December 2nd. While we can’t confirm whether the nature of this leak was real, the other approx. 35 leads they’ve shared were genuine and all resulted in a big hack they’ve made on an Israeli web hosting company called Signature-IT which hosted the sites of these entities (including government ministries, agencies, high profile businesses and others).
Cyberattacks in Israel
In Israel, the Israeli government officially said that an Iraninan cyber group is behind a cyberattack on an Israeli hospital in the north of Israel (named “Ziv”). In our recent updates, we have highlighted how Iraninan hacking groups are conducting attacks in Israel with this being one of them. The good news is – the attack wasn’t very successful and resulted in the same data leakage of patients, while the hospital remained functional. However the intention was to cripple the hospital with ransomware, although this was caught on time. The attack happened around Nov 27th, and a group named “Malik” (the one which attacked the “Ono” college at the beginning of the war) started to leak data of what they claim to be of 300,000 patients. The group had a Telegram page which was taken down shortly after they started to leak some data. Now, almost a month later, the government has issued an official statement saying Iran and its proxy Hezbollah are behind the attack, stressing they attacked a hospital during the war (the hospital is located not very far from the northern border where there are clashes between the IDF and Hezbollah since the beginning of the war).
Around the same time, there have been reports coming out of Iran on multiple gas stations taken down by what seems to be a cyberattack. There’s an unknown hacktivist group named “Predatory Sparrow” (“Gonjeshke Darande” in Persian, they have a Telegram group from today –