Palo Alto Networks recently released a blog, wherein it outlined how visiting clickbait websites and articles is inherently risky to users; mainly because these sites often use outdated or unpatched software making them vulnerable to compromise. Sites specializing in clickbait content exist for the sole purpose of generating ad revenue. These sites rely on traffic to generate revenue and use the following three strategies to boost traffic:
- Generative AI tools: Clickbait authors are increasingly using generative AI tools like Jasper and AIPRM that provide an easy method to generate SEO-optimized content to increase site traffic. Unit 42 found instances of automatically generated clickbait articles on websites running plugins that were at least 2 years out-of-date.
- Evergreen Topics: which people continue to be interested in regardless of triggers. Examples include personal finance, wealth, etc.
- Content Discovery Platforms: that often use techniques such as native advertising to disguise ads. Users find it tough to distinguish between the site’s original content and the ad content. Unit 42 found instances of clickbait articles that lured users into websites with plugins that were several months out-of-date.
All these tactics can be used to lure users into websites that aren’t concerned about the security of the user, but only care about the footfall. As such, they may often deploy out-of-date plugins or code.
“Some articles are just too tempting to not click on. But oftentimes, they’re the exact ones you should be avoiding. With the holiday season right around the corner, it’s only a matter of time before too good to be true deals under certain price ranges take over. Unfortunately, a lot of these articles can lead users to pages that deploy outdated code or older versions of plugins. Users should be mindful and keep an eye out for suspicious URLs, and ensure that their devices and browsers are up-to-date. A ‘think before you click’ mindset can go a long way to keep users safe when it comes to clickbait content”, said Anil Valluri, MD and VP, India and SAARC, Palo Alto Networks.
But how do attackers find these vulnerable websites? And how can the everyday users avoid such pages?
Finding vulnerable websites
To compromise any website, attackers must know the operating system, web-content management software (CMS), and any associated plugins and themes (aka the website’s web stack). Threat actors use this data to determine if a server is running out-of-date software or applications. With this information, they can easily find publicly known vulnerabilities and exploits. Such details can be gleaned through a website’s URL patterns, HTML content (found via Ctrl/Cmd+U on most browsers) and functionality.
For example, within a webpage’s HTML code, the following string: ‘wp-content/themes/Newspaper/style.css?ver=11.4.1’ indicates the site uses tagDiv’s Newspaper theme for WordPress—a potential concern given a vulnerability associated with it has been widely exploited (see below).
tagDiv’s Newspaper Theme Exploit
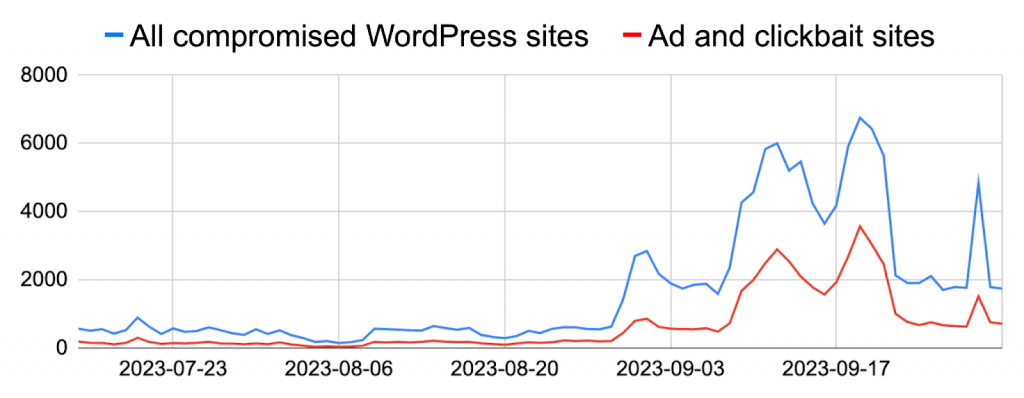
Recently, MITRE published a common vulnerability and exposure: CVE-2023-3169, for a vulnerability affecting tagDiv’s Newspaper themes for WordPress. Since then, sources have reported thousands of WordPress sites compromised through this vulnerability. Palo Alto Networks’ Unit 42 discovered approximately 10,300 compromised WordPress sites within a two-month period affected due to this CVE. A significant portion (30%) of these compromised sites were clickbait or ad sites (see graph below).
Other vulnerabilities
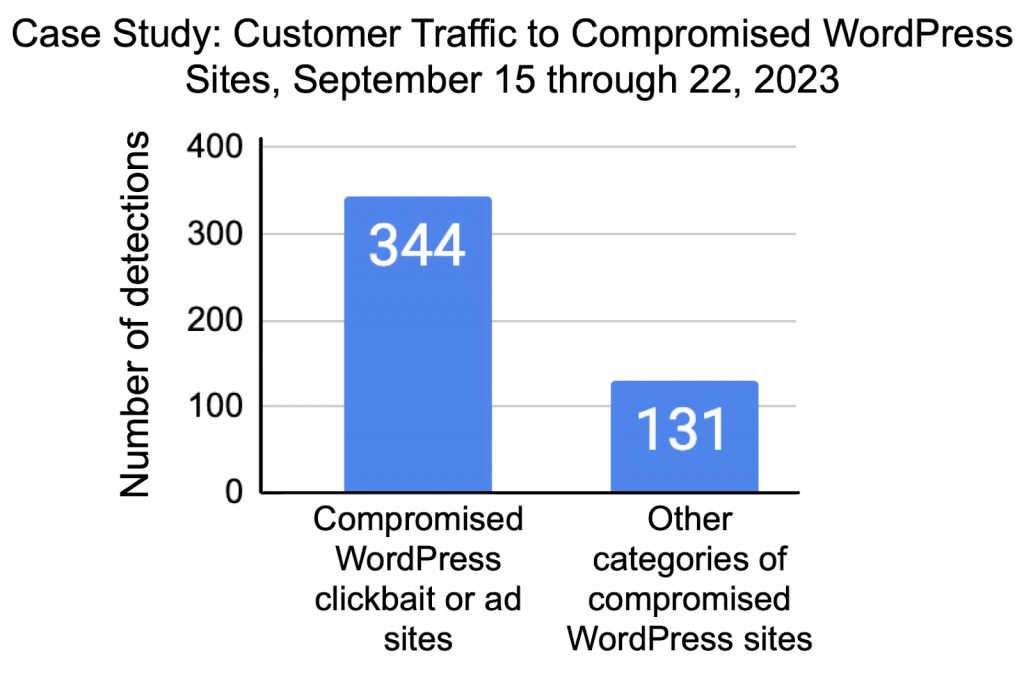
Apart from the aforementioned tagDiv Newspaper exploit, Unit 42 tracks websites for other vulnerabilities as well. During a case study from Sept. 15-22, 2023, they monitored a dataset of 1,600 randomly selected WordPress sites, detecting attempted visits by customers to compromised websites. The results indicated a nearly three to one ratio of compromised clickbait and ad sites compared to other categories (see graph below).