Check Point Research (CPR), the Threat Intelligence arm of Check Point® Software Technologies Ltd. (NASDAQ: CHKP), a leading provider of cyber security solutions globally, has released its ‘Cyber Attack Trends: 2021 Mid-Year Report’, which shows how cyber criminals have continued to exploit the global shift to hybrid working and target organizations across all sectors, including government, healthcare and critical infrastructure.
Organizations have experienced a 29% increase in cyber-attacks globally. The EMEA region showed the highest growth with 36%, followed by the Americas with an increase of 34% with APAC witnessing a 13% growth in attacks. This year has also seen a new ‘Triple Extortion’ ransomware technique emerge. While there have been successful international operations targeting cyber-crime, such as the take-down of the notorious Emotet botnet, threat actors launched sophisticated attacks which exploited organizations’ supply chains to cause widespread disruption.
Key trends revealed in the report include:
- Global increase in cyber-attacks: In 2021, US organizations saw an average of 443 weekly attacks, marking a 17% increase compared to earlier this year. In EMEA, the weekly average of attacks per organization was 777, a 36% increase. APAC organizations saw 1338 weekly attacks, a 13% increase. Specifically within Europe there was an increase of 27% while Latin America saw an increase of 19%.
- The rise of ransomware attacks and ‘Triple Extortion’: Globally, the number of ransomware attacks on organizations increased by 93% in H1 2021, compared to the same period last year. Increasingly, in addition to stealing sensitive data from organizations and threatening to release it publicly unless a payment is made, attackers are now targeting organizations’ customers and/or business partners and demanding ransom from them too.
- Supply chain attacks step up: The well-known SolarWinds supply chain attack stands out in 2021 due to its scale and influence, but other sophisticated supply chain attacks have occurred such as Codecov in April, and most recently Kaseya.
- The race to become Emotet’s successor: Following the botnet’s takedown in January, other malwares are quickly gaining popularity, namely: Trickbot, Dridex, Qbot and IcedID.
- Predictions for H2 2021: Ransomware will grow, despite law enforcement stepping up. Increased use of penetration tools to give live hackers ability to customize attacks on the fly and a trend towards collateral damage well beyond the initial target victim calls for a collateral damage strategy.
“In the first half of 2021, cyber criminals have continued to adapt their working practices in order to exploit the shift to hybrid working, targeting organizations’ supply chains and network links to partners in order to achieve maximum disruption,” said Maya Horowitz, VP Research at Check Point Software. “This year cyber-attacks have continued to break records and we have even seen a huge increase in the number of ransomware attacks, with high-profile incidents such as Solarwinds, Colonial Pipeline, JBS or Kayesa. Looking ahead, organizations should be aware of the risks and ensure that they have the appropriate solutions in place to prevent, without disrupting the normal business flow, the majority of attacks including the most advanced ones.”
Top predictions for H2 highlighted in the report include:
The war on Ransomware will intensify –Ransomware attacks will continue to proliferate despite increased investment from governments and law enforcement, especially as the Biden Administration makes this a priority. With such investment and ever more advanced tools, the authorities will enjoy some successes, but threat actors will evolve, and new groups will emerge in the ransomware arms race.
Man-in-the-Middle becomes the hacker in the network – Over the past two years, we have seen an acceleration in the use of penetration tools, such as Cobalt Strike and Bloodhound. These tools don’t just pose a real challenge from a detection point of view, they also grant live hackers access to compromised networks, allowing them to scan and scroll at will and customize attacks on the fly. Security professionals will need a whole new set of skills to detect this form of attack and prevent it from happening in the future.
Collateral Damage beyond the initial target – The growing trends of triple extortion, supply chain attacks and even just remote cyber-attacks may affect businesses more than ever. The triple extortion trend in ransomware now includes not only the original target organization, but also its customers, partners and vendors. This multiplies the actual victims of each attack and requires a special security strategy.
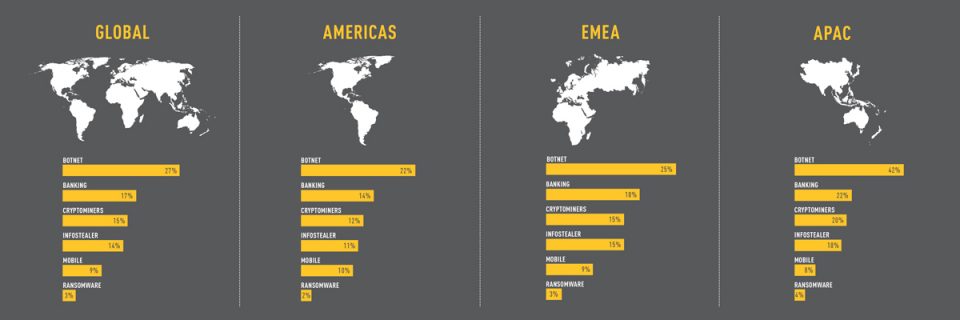
Cyber Attack Categories by Region in H1 2021:
Check Point provides zero-day protection with its networks, cloud, users and access security solutions. Our evasion-resistant technology maximizes zero-day protection without compromising business productivity. For the first time, businesses can reduce the risk of unknown attacks by implementing a prevent-first approach.