Worked with Regional CERT to Mitigate Threat
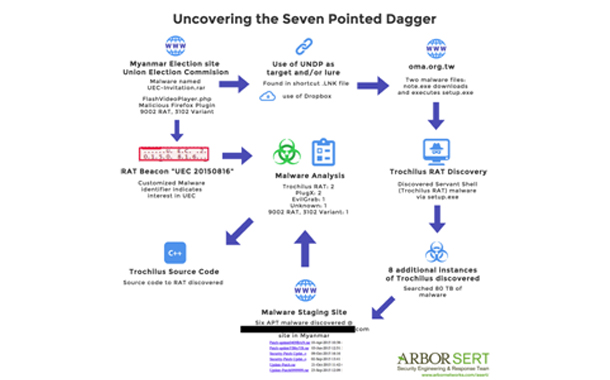
Arbor Networks released a new ASERT Threat Intelligence Report detailing an attack campaign involving various government websites and non-governmental organizations. This threat campaign involves a newly-discovered Remote Access Trojan (RAT) named ‘Trochilus.’ Believed to be driven by East Asian threat actors, Trochilus is part of a seven-piece malware cluster that offers threat actors a variety of capabilities, including espionage and the means to move laterally within target networks in order to achieve more strategic access.
This is the first instance of the Trochilus RAT observed by Arbor’s Security Engineering & Response Team (ASERT) on the global Internet. ASERT is unaware of any public reference to this malware being used in targeted threat campaigns.
In 2015, Arbor Networks and other research organizations discovered the PlugX and EvilGrab malware targeting government websites in Asia. After delivering initial findings to the regional Computer Emergency Response Teams (CERTs), additional malware was subsequently discovered and removed from related sites. The presence of new malware after the initial notification process from Arbor indicates an ongoing campaign and suggests persistent, resourceful actors are involved. In addition to updating security policies in Arbor’s products, ASERT regularly shares its operational insight with the threat intelligence and incident response community, hundreds of international CERTs and thousands of network operators around the world.
This ASERT Threat Intelligence Report includes a brief history of the Trochilus malware family, an overview of how the malware operates and a deeper technical analysis of the entire threat campaign to include PlugX, EvilGrab and the 9002 RAT malware also deployed.