By: Debojit Maitra, Ex – CISO, Aditya Birla Fashion and Retail Ltd. and Senior Cybersecurity Leader
Entropy is defined as a measure of randomness or disorder of a system. In a Statistical Thermodynamics Function that we use to measure the uncertainty or disorder in a System. The term disorder denotes the irregularity or lack of uniformity of a thermodynamic system.
Entropy Change can be defined as the change in the state of disorder of a thermodynamic system that is associated with the conversion of heat or enthalpy into work. A system with a great degree of disorderliness has more Entropy.
Entropy in Information Theory:
In Data science Entropy refers to the Degree of Randomness in a Data Set , which indicates how much uncertainty of Data in the Data Set. The Unit of Entropy is bit.
Under Information Theory Perspective Entropy represents the fewest bits it would take on Average to Transmit information in a Signal (ie a Random Variable)
Information Theory, the Entropy of a system represent the Lower Boundary of bits needed to represent Information:
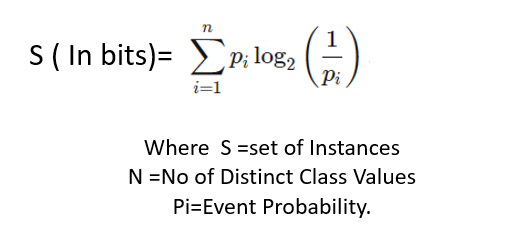
Entropy in Cyber Security:
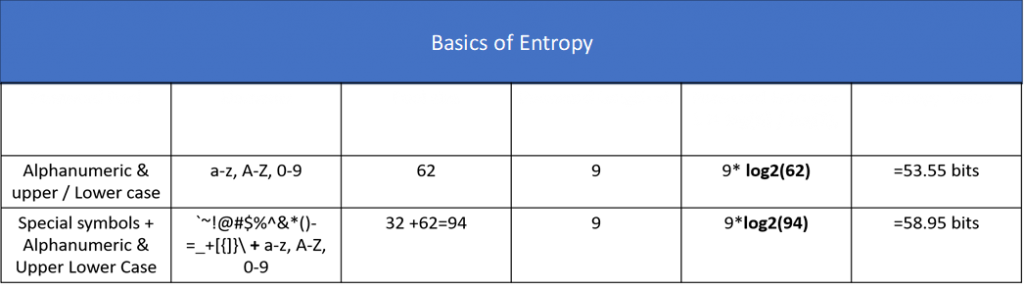
A Measure of the amount of Uncertainty an Attacker faces to determine the Value of a Secret or Crown Jewel. It is also a measure of unpredictability in a String of Data Set. A value having n bits of Entropy has the same degree of uncertainty as a uniformly distributed n-bit random value.
Encrypted Data is high-Entropy, making it easily identifiable from more ordered data, such as text or code. On the other hand, poorly encrypted data has lower Entropy, providing a hint that a particular ciphertext may be breakable.
So higher the Entropy , the more difficult for an Attacker to Guess the Input Data.
Entropy in Crypto system:
In Zero Trust SDP we use Entropy to produce several random numbers, which in turn helps to create security keys for protecting sensitive information. Now, the security value of the key depends on the quality of random number generation. Both compression and encryption schemes increase the entropy of plaintext because there are not as many patterns present as in natural language.


Entropy and Modern Crypto System:
- Entropy Source
Entropy Sources are Physical sources of Information whose O/P Appears to be Random. They are used as I/P to either a Random Number Generator ( RNG) or Pseudo Number Generator ( Sequence of Number ) ( PNG).
- Random Secret Keys
We take Plain Text Message and Encrypt it with various tool and Generate Cipher Text but most of the time this Encryption is not absolutely Secured and Attackers manage to extract meaningful Information from this.
In cryptography, a semantically Secure Cryptosystem implies that any information of the Plain Text based on Cipher Text and its length cannot be feasibly extracted.
Entropic Security of an Encryption Key is similar to Semantic Security when Message Spaces have highly Entropic distribution.
In Information theory Entropy is a measure of unpredictability of Information in message. It is the expected Value of Information in a Message. Randomness is a measure of uncertainty in an Outcome and thus Applied to the concept of Information Entropy.
What is Role of Entropy in Cyber Security?
- Entropy is an important concept in cyber security because it can be used to measure the strength of algorithms and cryptography. In order to effectively protect data, algorithms must be strong enough to withstand attacks, and Entropy is one way to measure this strength. Entropy can also be used to measure the security of communication networks, as well as to detect malicious activity.
- It is used to measure the amount of randomness in passwords, encryption keys, and other Data used for security purposes. Entropy is important for cyber security because it helps to ensure that data is secure and can’t be easily guessed or broken into.
- It used to measure the Randomness in relation to the Area that require Random Data, like Code Obfuscation and Data Compression.
About the Author
Debojit is the Ex – CISO, Aditya Birla Fashion and Retail Ltd. and Senior Cybersecurity professional. He has worked in the domain of financial risk management for three decades. He works on effectively monitoring and maintaining the security of their organization’s applications, databases, computers, and websites. He is a Graduate in Electronics and Telecommunication. In his career of more than 30 years, he has worked with many large companies including HLL, Tata Nelco, RIL and Aditya Birla. He has received many prominent awards including CISO World, CIO & Leader, Enterprise IT World CIO Axis and CISO, etc. Connect


