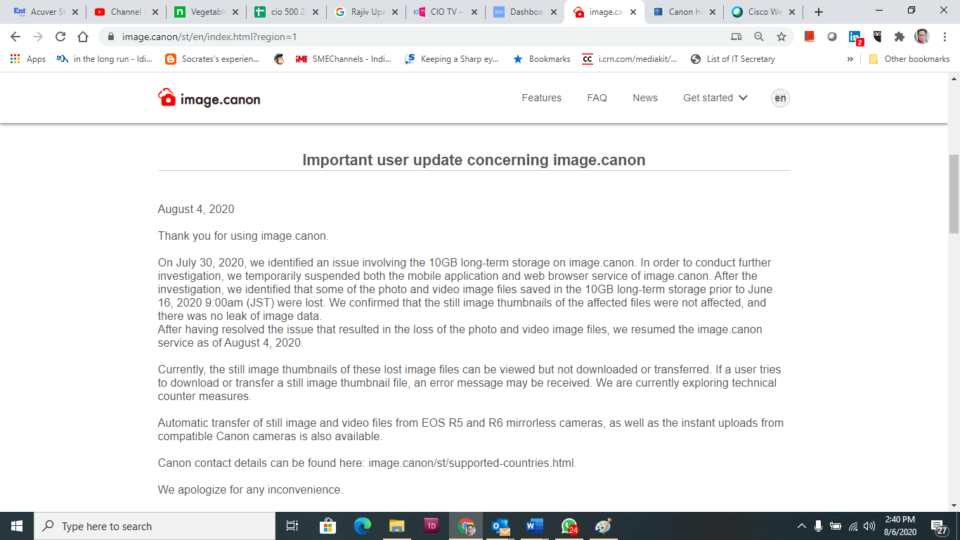
After infamous Maze Ransomware attack on Cognizant a quarter back, the notorious virus has again come to action. This time it has made the global documentation and printer company Canon its victim. It is believed that it has crippled latter’s numerous services, including email, Microsoft Teams, USA website, and other internal applications, which has been reported by BleepingComputer. The website further adds that the company has lost 10TB Data, which was assigned to its cloud photo and video storage services – image.canon. This news has also been corroborated by image.canon landing page, where there is a declaration that the website has lost data and explains, “On July 30th, 2020, we identified an issue involving the 10GB long-term storage on image.canon. In order to conduct further investigation, we temporarily suspended both the mobile application and web browser service of image.canon. After the investigation, we identified that some of the photo and video image files saved in the 10GB long-term storage prior to June 16, 2020 9:00am (JST) were lost. We confirmed that the still image thumbnails of the affected files were not affected, and there was no leak of image data. After having resolved the issue that resulted in the loss of the photo and video image files, we resumed the image.canon service as of August 4, 2020. Currently, the still image thumbnails of these lost image files can be viewed but not downloaded or transferred. If a user tries to download or transfer a still image thumbnail file, an error message may be received. We are currently exploring technical countermeasures.” Till now the website is not fully functional though.

Reacting to it, John Shier, Senior Security Advisor, Sophos, said, “The ransomware attack on Canon is yet another example of the Maze gang’s sustained and brazen targeting of enterprises. Following other recent high-profile attacks, this latest salvo should be a wake-up call to all the enterprises who haven’t taken the time to assess their security posture and bolster their defenses against these pernicious adversaries.”
“Many of these attacks start by exploiting external services or simple phishing campaigns. The successful campaigns will often be followed by living-off-the-land techniques, abusing over-privileged and under-protected accounts, and hiding in plain sight.
“Enterprises must take the time to ensure they’ve built a strong security foundation (e.g. principle of least privilege, MFA everywhere, patching, user training, etc.), which includes investment in both prevention and detection technologies today if they don’t want to be a victim tomorrow.”