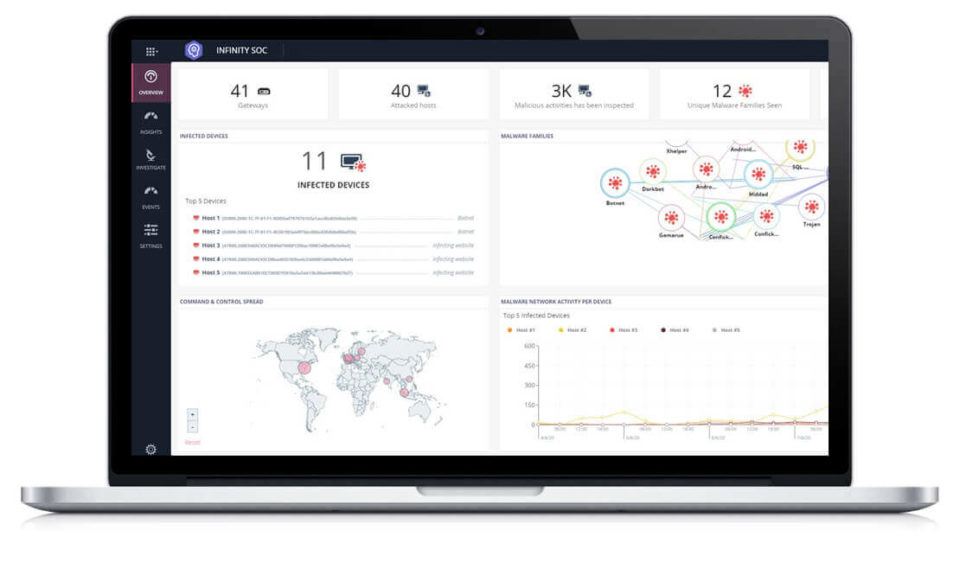
Check Point Software launches Infinity SOC, which unifies threat prevention, detection, investigation and remediation in a single platform to give unrivalled security and operational efficiency. Infinity SOC is used daily by the Check Point research cyber analysts, to expose and investigate the world’s most dangerous and sophisticated cyber-attacks. It uses AI-based incident analysis to filter millions of irrelevant logs and alerts, helping enterprise security teams to expose and shut down cyber-attacks with best-in-class speed and precision.
Security Operations Centre (SOC) teams at a majority of organizations struggle to identify and mitigate malicious activity on their complex network estates, because they use multiple point products that generate millions of event logs and alerts daily. In a SOC survey*, 68% of respondents stated that up to half of the events they analyse are false positives. As a result, critical attacks are often undetected until it is too late. 98% of IT security professionals reported SOC-related challenges, with the leading operational challenges being the manual work involved in analyzing and remediating incidents (cited by 52%), accurately identifying the most critical events (52%), and an overload of logs and alerts (51%).
Check Point’s Infinity SOC solves these challenges and helps enterprises protect their networks by delivering:
- Unrivalled accuracy to quickly shut down real attacks: it automatically exposes even the stealthiest attacks from millions of daily logs and alerts with unrivalled accuracy, powered by industry-first AI incident analysis. Infinity SOC automatically triages alerts to enable quicker respond to the critical attacks and offers single click remediation with a lightweight client on the infected host. It also prevents hackers from launching phishing campaigns against users by taking down lookalike corporate web and email domains.
- ● Rapid incident investigations: Infinity SOC is powered by ThreatCloud, the world’s largest collaborative network to fight cybercrime, enabling teams to quickly search for in-depth live intelligence on any indicator of compromise, including global spread, attack timelines and patterns, malware DNA and more. This also includes deep-link searches on social media and OSINT to deepen investigations – unlike other solutions, which use offline threat databases. Suspicious files are quickly checked using SandBlast threat emulation, which has the industry’s best malware catch rate.
- ● Zero-friction deployment: Infinity SOC is a single, centrally managed cloud platform, improving teams’ operational efficiency and reducing TCO. It deploys in minutes, and avoids costly log storage and privacy concerns with unique cloud-based event analysis that does not export and store event logs.
“It was critical for us to find a solution to help us cut through the daily deluge of alerts and events and find the handful of genuine, potentially damaging threats to our networks,” said Soren Kristensen, Security Engineer at Terma A/S. “Infinity SOC delivers exactly that, and more. It has enabled us to filter out all the irrelevant alerts and background noise so we can see the true state of security across our network, and to automate processes, which enables us to focus on the activities that really matter. It also gives us threat intelligence and hunting capabilities that we simply didn’t have previously.”
“Infinity SOC enables security teams to cut through the daily overload of event alerts, and eliminates network blind spots to automatically pinpoint and block the most sophisticated attacks before they can cause damage,” said Itai Greenberg, VP of Product Management at Check Point. “Its advanced AI-based analytics, powered by the industry’s most advanced threat intelligence resource, filters millions of alerts into the handful of critical, genuine threats so that analysts can makes the fastest, most targeted responses possible to safeguard their organization. No other solution offers Infinity SOC’s combination of automated prevention, detection, investigation and remediation capabilities in a single platform.”